| | Summary: People who use multiple devices with wireless communication capabilities (like mobile phones, PDAs, laptops, etc.) know the problem of having all these devices communicating with each other easily, i.e. ad-hoc and without complex configuration efforts. All these devices form a so called "Personal Area Network" (PAN) and it's assumed that the importance of those networks will increase as more such devices become available at lower prices both for the user (like mom and dad at home) and for businesses (like shops, restaurants, etc.). People who use multiple devices with wireless communication capabilities (like mobile phones, PDAs, laptops, etc.) know the problem of having all these devices communicating with each other easily, i.e. ad-hoc and without complex configuration efforts. All these devices form a so called "Personal Area Network" (PAN) and it's assumed that the importance of those networks will increase as more such devices become available at lower prices both for the user (like mom and dad at home) and for businesses (like shops, restaurants, etc.).
The more they are used, the higher is the importance to establish some security features within these networks, like e.g.:
- Identity Management: As every communicating instance has in some way an identity, they have to be managed so that all communicating parties know about them somehow without having every party to manage them itself but also without giving up privacy
- Access Control Management: Not everybody may be allowed to access every device, so somehow these access rights have to be managed
- Reputation Management: Over time, a user or device that behaves well will get a good reputation within a certain community so it may be more trustworthy than a completely unknown user/device or someone who behaved badly in the past. (This is the main focus of our project "Anonymous Reputation Management in Social Networks")
- Charging Management: Businesses want to make money out of their services, so somebody has to deal with charging the use of them
All this establishes a so called "security context" around the user of a PAN, and consequently it's called a "Secure PAN" (SPAN).
The goal of our SPAN project is to explore some difficulties which arise within these kind of networks. What happens if only some devices are connected directly to the Internet so that they have to act as a relay for all the others? How to deal with identities and access rights without directly accessing a database of them? How to have mobile and fixed devices interact seamlessly? (This is called "Fixed Mobile Convergence".) What about securing connections between devices that never met before? How to minimize the need of user intervention without lowering the strength of security? How to centralize the control over identities and access control in a way that makes it more easily to setup new services without giving up security?
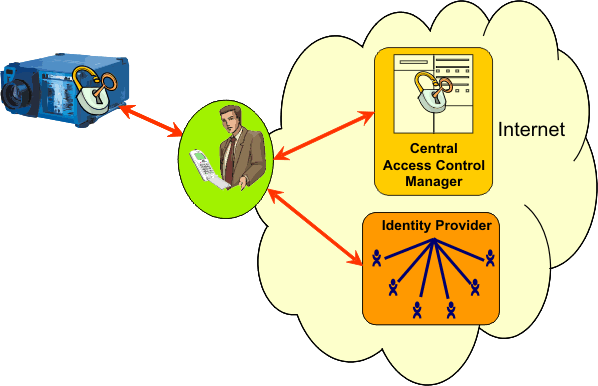
We build a proof-of-concept scenario where all these questions can be studied. Our application consists of a beamer which some person wants to use, but without prior knowledge of each other and also without allowing a third party (some malicious attacker) to disturb them. Two other entities involved are a Identity Provider, which is essentially a database with the knowledge of the users identity, and an Access Control Manager, which is a system authorized to decide who may use the beamer and when.
Our implementation uses techniques which are commonly known in the mobile and security communities such as J2ME (for running code on the mobile phone), Bluetooth and GPRS (wireless communication techniques), IP, TCP, BEEP and SOAP (communication protocols), SSL/TLS and SAML (for securing all communication and exchanging security information). We implement the part of the mobile phone on a Sony/Ericsson W800i and the other entities (Identity Provider, Access Control Manager and the beamer control itself) on Debian GNU/Linux systems.
Further Details:Publications: |
